
|
Home
| pfodApps/pfodDevices
| WebStringTemplates
| Java/J2EE
| Unix
| Torches
| Superannuation
|
| About
Us
|

|
Secret Key Generator
|
by Matthew Ford 4th July 2018 (original
15st June 2013)
© Forward Computing and Control
Pty. Ltd. NSW Australia, All rights reserved.
The java application available here, will generate essentially 'random' 128 bit keys, encode as hex digits, for use with SipHash Secure Challenge and Response for micro-devices (AVR / Arduino). The application also has the option to save the key's hex digits in a QRcoded image. This simplifies loading this long key into the pfodApp on your Android mobile.
To run the application, download the jar file, SecretKeyGenerator1_0_3.jar. Save it in a directory which you can write to.
You should double click on the jar file and it should run. If not, you do not have Java installed. To install Java goto www.java.com and download and install the Java runtime.
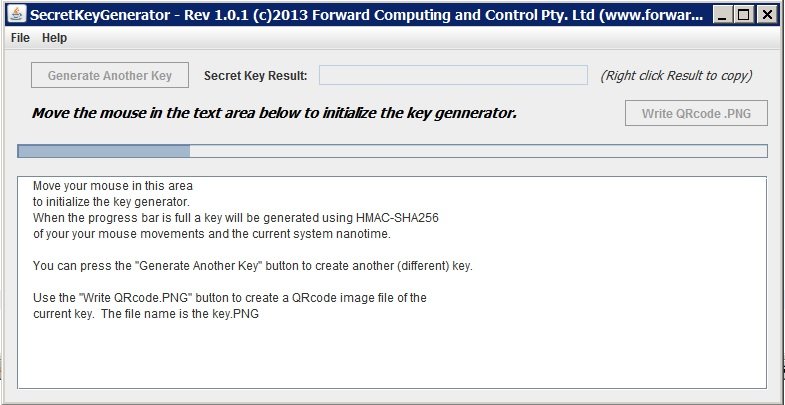
Put the downloaded SecretKeyGenerator1_0_3.jar file
in a directory.
Then from a terminal window, change directory to
where the SecretKeyGenerator1_0_3.jar file is and run the command:-
java -jar SecretKeyGenerator1_0_3.jar
If the above window does not appear, goto www.java.com and download and install Java.
As well on Mac OS, you can assign "Jar Launcher"
as the default app. to use when you double-click a jar file, as
follows (I don't believe you need the developer tools installed for
this):
i) Click once on the .jar file in the Finder and then from
the menubar in the Finder select File -> Get Info".
ii)
Click on "Open with" and from the popup menu select
"Other". A file browser window will open.
iii) In this
window, go to the /System/Library/CoreServices folder and select 'Jar
Launcher'.
iv) Then make sure the "Always Open With"
checkbox is checked and then click Add.
v) Then click the "Change
all" button so that any jar file will be opened
automatically.
vi) Finally, close the Info window and now when you
double-click any of your jar files they should run
automatically.
(see
http://macosx.com/tech-support/how-to-execute-a-jar-file-in-os-x/9549.html
)
As mentioned in SipHash Secure Challenge and Response for micro-devices (AVR / Arduino), in order to be secure, the key must be long and un-guessable. The 128 bit keys generated by SecretKeyGenerator1_0_3.jar, are generally believed to resistant to brute force attacks, which try all possible combinations of the secret key. The other means of attack is to guess the key based on some other knowledge.
This Key Generator, produces an essentially 'random' key, which means one key is a likely as another as far as both you and any attacker can tell. To initialize the key generator, you move your mouse around in the text window. When the progress bar if full a key is generated from your mouse movements and the computer's current nano time. The generated key is the first 16 bytes of the resulting hash.
When you press the Generate Another Key button, a completely new key is generated from your mouse movements and the computer's current nano time.
The key produced is essentially unique and un-reproducible, because even with the exact mouse movements, the nanoSec time will be different next time. Each press of the Generate Another Key button produces a different key.
To simplify entering the generated key into the Android pfodApp, the SecretKeyGenerator, also allows you to save the key as a QRcode image. The .PNG image will have a file name of the key it contains. Attaching this image to the device protected by this key, allows users to scan the QRcode directly into the pfodApp's connection password field using the Scan QR button.

b0Ux9akSiwKkwCtcnjTnpWp.PNG
This application includes hash
code from http://www.gnu.org/software/gnu-crypto/
and QRcode from http://code.google.com/p/zxing/
under their respective licences
AndroidTM is a trademark of Google Inc, For use of the Arduino name see http://arduino.cc/en/Main/FAQ
The General Purpose Android/Arduino Control App.
pfodDevice™ and pfodApp™ are trade marks of Forward Computing and Control Pty. Ltd.
Contact Forward Computing and Control by
©Copyright 1996-2020 Forward Computing and Control Pty. Ltd.
ACN 003 669 994